Knowledge Center
Wireless and RF Communications
This is just a sample of this page's content: View the full page
Distributed Computing for IoT: Data Management in a Fog Computing Environment
Mobile cellular operators are making plans for Mobile Edge Computing (MEC), which enables Cloud computing capabilities and an IT service environment at the edge of the cellular network. It is a concept developed by ETSI (European Telecommunications Standards Institute) that aims to bring computational power into Mobile RAN (radio access network) to promote virtualization of software at the radio edge. MEC brings virtualized applications much closer to mobile users ensuring network flexibility, economy and scalability for improved user experience.
Related Courses :
- Onsite Training: Emerging Technologies, SDN, NFV, Cloud, Blockchain and General Networking
- Onsite Training: 5G Wireless, M2M, IoT, SDN, NFV, Cloud
- Onsite Training: Defense, Security, Public Safety
- Onsite Training: IoT, IPv6, VoIP, EoIP, IMS, MPLS, SNMP
- Onsite Training: M2M, WiFi, Bluetooth, Zig Bee, IoT
Check out our courses on 5G Wireless technologies, applications, and marketplace along with related courses on M2M and IoT.
LTE Advanced: A Quick Look at Releases 10 to 12
Emerging trends such as social networking, cloud computing and storage, and video sharing, together with mobile computing will continue to put an enormous pressure on the cellular infrastructure. It is anticipated that at least a 30 fold increase in capacity, as well as additional services that will enhance the user experience, are required to make it all work. The LTE-A advanced project was initiated to meet this increasing traffic demand.
Related Courses :
The Eogogics LTE Curriculum …
… includes two dozen courses covering such topics as LTE Advanced/LTE RAN and Core, Design and Optimization, LTE Evolution to 5G, VoLTE, LTE-IMS Inter-work, LTE for Public Safety, and much more.
e-Learning Course - LTE Technology: For Technical Audiences (6 hours long)
This is a web-based video recording of the 6-hour long course webcast live on Dec. 10-11, 2009. It’s aimed at technical audience involved in the design and deployment of LTE networks, equipment, or software.
e-Learning Course - LTE Explained: For All Audiences (3 hours long)
This is a web-based video recording of the 3-hour long course webcast live on Nov. 4, 2009. It is aimed at the non-engineers involved in business planning and forecasting, policy making and regulation, marketing and sales, management, and procurement for the advanced 4th generation wireless networks.
Related Courses :
Spot Light on LTE Curriculum
Given the number of queries we get daily on LTE, I thought it’d be good to summarize what we’ve got, and it’s a lot: 20+ courses available for private classes (at your offices or WebLive™) and a growing e-learning collection open to individuals.
e-Learning - WiMAX Short Course
PDF of a 43-slide, narrated Power Point e-course, addressed to technical audiences that provides a short introduction to the WiMAX (IEEE 802.16) network architecture, physical layer, and MAC layer.
Related Courses :
The Eogogics WiMAX curriculum includes courses on WiMAX and Mobile WiMAX, WiMAX network design/optimization, and WiMAX traffic/capacity engineering.
e-Learning - WiMAX Explained for All Audiences (3 hours long)
This is a web-based video recording of the 3-hour long course webcast live on Oct 22, 2009. It is aimed at the busy executives and non-engineers involved in business planning and forecasting, policy making and regulation, marketing and sales, management, and procurement for the advanced 4th generation wireless networks.
e-Learning - 4G Technologies & Services: For All Audiences (3 hours long)
This is a web-based video recording of the 3-hour long course webcast live on Oct. 21, 2009. It is aimed at all audiences new to 4G, nontechnical or nontechnical, who wish to learn what 4G is all about.
Related Courses :
3G, IMS, and the Evolution of Carrier Network Economics
It’s not easy to be a mobile industry executive in a developed country at this time. As a matter of fact, a wireless exec’s life has never been more complex. Just when the wireless carriers are starting to look at service differentiation made possible by 3G technologies, the subscriber penetration is starting to slow and the shareholders are starting to ask for higher OBIDA margins.
Related Courses :
Paul’s Puzzler: Mission Impossible!
Can the receiver obtain the correct packet after one or more retransmissions, without it ever being received correctly? This may seem like “Mission Impossible”. To figure out whether it is or not, we’ll consider a brain teaser. You may have run into a version of this teaser before, but here is the version suited to the discussion of the problem at hand.
Related Courses :
The Internet of Things (IoT) Revolution: Are You Ready?

Powered by the expansion of connectivity fueled by IPv6, the Internet is quickly morphing from a ‘network of computers’ into a ‘network of things’, and this technology is developing at a much faster pace than other such technologies of the past. Smart phones, cars, homes, buildings, wearable computing devices, unseen but ubiquitous sensors embedded into appliances, equipment and infrastructure, and many other “things” (including living things such as cattle and wildlife) are all getting linked up into a vast and pervasive Internet of Things (IoT)! It’s a disruptive technology that — though largely invisible to consumers — will have profound impact on our everyday lives, how businesses operate, and on the world economy as a whole (multi-trillion dollars) — all in as little as five to 10 years.
Related resources:
Article: Distributed Computing for IoT: Data Management in a Fog Computing Environment
Course: Internet of Things Workshop
Research publications on IoT (look for ‘IoT’ in our Store‘s ‘Search Product’ field)
Nearly every industry vertical stands to be transformed by the coming IoT revolution. The IoT technology is creating enormous opportunities for new services as well as more efficient delivery of existing services. The rapid pace at which this technology is evolving is also giving rise to major privacy/security risks for individuals, institutions, and public infrastructure — creating new vulnerabilities and giving rise to not-as-yet-thought-of attack modalities, including those of remotely engineered death and destruction. Yet, many businesses and government agencies wonder if this is all passing hype — which it is not — and many do not know how the IoT should fit into their organizational strategy.
So is your organization positioned correctly to benefit from this coming Internet of Things (IoT) revolution? Starting with this issue of the Eogogics Quarterly, we will be publishing a series of articles, courses, and research publications to help our readers better understand the underlying technologies, business and societal impact, potential, and market landscape of the Internet of Things (IoT). Featured in this issue are an article on distributed computing for the IoT and an update on the new courses and research publications on IoT that have been recently added to our product line-up. Are there IoT issues you’re interested in that are not covered by our courses and research publications? Call us (+1 703 345-4375) or drop us a line at info@eogogics.com. We may be able to help.
Telecommunications
This is just a sample of this page's content: View the full page
SDN/NFV: Enhancing Network Capacity and Functionality
SDN and NFV have been developed to help meet the challenge of increasing demand for services and user expectation of rapid provisioning and universal availability. Both rely on virtualization, the ability to make a piece of equipment look like another via the magic of software. SDN was originally developed to address the problems of large data centers, where virtualization of hardware and operating system is important. It will likely spread to other areas, including the WAN, where virtualization and the ability to dial up bandwidth and related characteristics would be extremely valuable as well. NFV is an outgrowth of SDN in many respects, concentrating on backbone networks, where the need to rapidly reconfigure resources is key.
Related Courses :
Blockchain and Other Cutting Edge Tech
Blockchain, the Distributed Ledger Technology behind Bitcoin, has attracted interest across many industries including financial services, legal, real estate, digital rights, identity management, healthcare, asset tracking, supply chain management, and the Internet of Things (IoT). A disruptive technology, it has the potential to transform the way many transactions are conducted.
Related Courses :
Optical Networking: Past and Future
Light-based methods have been used for information transmission for thousands of years. Probably the earliest method is the fires that have been used for signaling since Biblical times.Smoke signals have been used for communications for a long time, most notably by Native Americans. Lanterns hung in Boston’s Old North Church ("One if by land, and two if by sea") figure prominently in Paul Revere’s famous midnight ride in 1775.
Related Courses :
Distributed Computing for IoT: Data Management in a Fog Computing Environment
Mobile cellular operators are making plans for Mobile Edge Computing (MEC), which enables Cloud computing capabilities and an IT service environment at the edge of the cellular network. It is a concept developed by ETSI (European Telecommunications Standards Institute) that aims to bring computational power into Mobile RAN (radio access network) to promote virtualization of software at the radio edge. MEC brings virtualized applications much closer to mobile users ensuring network flexibility, economy and scalability for improved user experience.
Related Courses :
- Onsite Training: Emerging Technologies, SDN, NFV, Cloud, Blockchain and General Networking
- Onsite Training: 5G Wireless, M2M, IoT, SDN, NFV, Cloud
- Onsite Training: Defense, Security, Public Safety
- Onsite Training: IoT, IPv6, VoIP, EoIP, IMS, MPLS, SNMP
- Onsite Training: M2M, WiFi, Bluetooth, Zig Bee, IoT
Check out our courses on 5G Wireless technologies, applications, and marketplace along with related courses on M2M and IoT.
e-Learning Course - MPLS Backbone for Technical Audiences (6 hours long)
This is a web-based video recording of the 6-hour long course webcast live on Oct 28-29, 2009. It’s aimed at those who wish to develop a deeper understanding of Multiprotocol Label Switching (MPLS), related issues, and the competition.
Related Courses :
MPLS and the Evolving Telecom Landscape
By 2010 both ATM and FR were in fairly steep decline, relegated to the status of legacy technologies. MPLS usage is growing and new applications for it continue to emerge, making it the technology of choice for most large-scale networks. Nowadays the great buzzword is “cloud computing”, with different versions such as Software as a Service (SaaS—Gmail, Google maps, YouTube, Facebook), Platform as a Service (PaaS—Amazon Elastic Compute Cloud, Windows Azure, Salesforce). All of these utilize MPLS-based networks.
Related Courses :
Good Mobile Backhaul: There's No App for That!
Mobile backhaul and wireless backhaul are two names for the same thing: the communications link between the practically ubiquitous cellular antennas on radio towers, buildings, highway signs, church steeples, fake Sequoyah trees and elsewhere that connect mobile subscribers to the carrier IP network and/or Internet.
Our Comprehensive Mobile Wireless Backhaul Curriculum
Includes making a business case for backhaul, application case studies, market, technology deep-dive, and security
Tutorial: Internet Multimedia Subsystem (IMS)
Communications networks are rapidly evolving into policy-based, packet-oriented networks designed to provide a particular quality-of-services (QoS) for subscribers while reducing the costs associated with capital expansions, network operations, and management. If you are involved with telecommunications planning, engineering, deployment, strategy, marketing, or services creation, it is critical that you understand the technology and business implications of IMS.
Related Courses :
e-Learning Course - NextGen Networks (NGN) Explained: For All Audiences (3 hours long)
This is a web-based video recording of the 3-hour long course webcast live on Oct 21, 2009. It’s aimed at those who need a quick, “technical light” introduction to Next Generation Networks (NGN).
The Three C’s of VoIP: CODECS, Codes, and Convicts!
Anyone who has ever been engaged most certainly can list the four “Cs” of diamonds: Color, Clarity, Cut and Carat weight. But did you know that there are also three “Cs” of Voice over IP?
Related Courses :
Eogogics Courses on Multimedia Technologies
Check out our multimedia curriculum for courses on IMS, SIP, VoIP, and EoIP.
TV Studios, Airborne Military Platforms, James Bond … and SNMP
Do you know what the following have in common: television broadcast studios, automated fare collection systems, airborne military platforms, energy distribution systems, and emergency radio networks? It’s SNMP, a protocol designed to manage a diverse set of networked equipment.
Related Courses :
Tutorial: Simple Network Management Protocol (SNMP)
Simple Network Management Protocol (SNMP) is a widely used protocol designed to facilitate the management of networked devices from a central location. Designed originally for the management of devices such as routers and switches, its usage has grown rapidly to encompass the monitoring of nearly any electronic device one can think of.
Related Courses :
SDN/NFV (Software Defined Networking, Network Functions Virtualization): Networking Game Changers?

The terms SDN and NFV have acquired magical connotations for those who work with networks but are not technical, raising many expectations. Are SDN and NFV really such a game changer for networking? SDN and NFV are among the half dozen or so technologies seeking to address the issues that trouble contemporary networks. The other major technologies in the play include GMPLS, ASON, high-speed Ethernet, NGN, and OTN, with a good deal of overlap between the various solutions that have been proposed.
In this issue of the Eogogics Quarterly, focused on SDN and NFV, we share a number of free knowledge resources with you:
- You can read this article for a great introduction to Virtualization, SDN, and NFV, including the concepts that underlie these technologies, how the technologies work, their interrelationships, applications, benefits, and their future
- You can download this tutorial (PDF) on SDN and NFV
- Or watch this interactive web-presentation (“Sway”) on SDN and NFV
If you are looking for onsite courses (available for presentation worldwide) or research publications on SDN and NFV, take a look at:
- Onsite course on SDN
- Onsite course on SDN and NFV
- Market intelligence research publications on SDN and NFV (for our full research lineup, check out our Store)
So are SDN/NFV game changers for the networking industry? Take a second to create a free Eogogics account (using the blue ‘Join/Log in’ button up top), then post your comments to this blog and let us know. The free account will also give you access to free educational resources and discounts. It’s clear though that SDN and NFV are here to stay and grow in application and importance! If you’d like to learn more about them, this website is a good place to get started.
Technologies
This is just a sample of this page's content: View the full page
MOOCs: A Revolution … or Just Plain Hype?
As of this writing, hundreds of MOOCs are being offered by US and foreign universities and millions of people have registered for them. But are they effective? They have been criticized for their lack of academic rigor. They also suffer from poor completion rates, with the bulk of participants dropping out in the first few days of the course. But they do offer the promise of making higher education and degrees accessible to a much larger chunk of the world’s population at a fraction of the cost, significantly reducing the cost of corporate training, and providing a convenient and cost-effective option for lifelong learning.
Blockchain and Other Cutting Edge Tech
Blockchain, the Distributed Ledger Technology behind Bitcoin, has attracted interest across many industries including financial services, legal, real estate, digital rights, identity management, healthcare, asset tracking, supply chain management, and the Internet of Things (IoT). A disruptive technology, it has the potential to transform the way many transactions are conducted.
Related Courses :
Why a PM Certification Program May Not Translate into an Improved Project Success Rate
There are many possible roles in a project. The obvious ones include the project sponsor who pays for the project, the project manager (PM) who directs the project, and various project team members who perform project work.
Related Courses :
Eogogics Technical and Project Management Curriculum
This curriculum includes nearly two dozen courses on technical management, project management (including courses that meet the PMI certification requirements), engineering economics, cost reduction, and related management topics.
Decision-Making Tools: Expected Monetary Value (EMV)
EMV is a balance of probability and its impact over the range of possible scenarios. If you have to make a decision between two scenarios, which one will provide the greater potential payoff?
Related Courses :
Computing in the Cloud: A Practical Review
Cloud computing appears simple but is very complex. The apparent simplicity has caused many organizations to move to cloud computing somewhat blindly, driven largely by promises of simplification which will result in cost savings, or just sheer cost savings. Cost savings alone is often enough cause for celebration. And, interestingly, the results achieved by those organizations who “just go for it” are, unexpectedly, usually very positive.
Related Courses :
Root Cause Failure Analysis: Reducing Costs and Increasing Customer Satisfaction
You know the problem: You’ve had a product in production for years with recurring failures you can’t seem to stop. Your people say it’s inherent to the product, and there’s nothing you can do about it. Production continues and so do the failures. You get to watch a sizeable chunk of your profits continue to move from the production line to the scrap bin.
Related Courses :
Eogogics Reliability Engineering Curriculum
This curriculum offers courses and workshops on FMEA, Root Cause Failure Analysis (RCFA), Design of Experiments, and Industrial Statistics, besides an overview course on Reliability Engineering.
Statistical Tolerance Analysis
Dimensional tolerances specify allowed variability around nominal dimensions. We assign tolerances to assure component interchangeability while meeting performance and producibility requirements. In general, as tolerances become smaller, manufacturing costs become greater.
Related Courses :
GD&T Demystified
To better define a part, Geometric Dimensioning and Tolerancing (GD&T) is often used as a symbolic way of showing specific tolerances on drawings. GD&T is a valuable tool that effectively communicates the design intent to manufacturing and inspection.
Related Courses :
Web Classes: NGN, MPLS, IMS, SIP, VoIP, EoIP/VoIP, IPTV, 3G LTE/4G, WiMAX, OFDM, MIMO, SDR, FMC ….
“Why don’t you offer online classes on emerging telecom technologies, so those of us who’re too busy to travel to public classes can keep up with the industry?” asked a fellow telecom exec in a recent conversation. “Aren’t there plenty of companies already offering free webinars?” I asked. “Yeah, but it’s not training. They’re all selling something: hardware, software, tools, or whatever” he countered.
Related Courses :
Contradictions: A Tool for Systematic Innovation

The Quest for a Killer App for Identifying Problems and Generating Solutions
Through the first 20 years of my engineering career, I unsuccessfully sought the “killer app” for Systematic Innovation (“SI”). Each time I began employment with a heavy-hitter organization (such as the US Air Force Research Lab, Johnson and Johnson, Philips, and Intel Corp.), I enquired if they had a systematic problem deconstruction and solution generation methodology at the ready to help me join the ranks of the world-class problem solvers who were surely responsible for their standing in the industry. Each time the answer was, “No, but you’ll figure it out, that’s what engineers do”.
After having acquired a lot of problem-solving experience with complex systems, I began to see why it might be difficult to conceive, let alone develop, a general methodology that could help you understand the workings of a complex system (in fields as diverse as microbiology and nuclear engineering), then allow you to systematically develop effective solutions to its problems.
But wait, such problem-solving systems do exist for some fields! We do not have to look further than mathematics, chemistry, statistics, and other such areas. What do such disciplines have in common? They all shift the analysis from the real to the abstract world and then back again during solution generation. Can we not develop a methodology that generalizes the approaches used in such disciplines to allow us to apply it to any type of system?
Good Things Come to Those Who Wait
Having spent 20 years in the industry, I finally discovered that elusive “killer app.” Around ten years into my employment with Intel, a relatively new methodology called TRIZ was introduced into the company. TRIZ (an acronym for the Russian equivalent of “The Theory of Inventive Problem Solving”), is based on a long-running study of over four million patents from the worldwide patents data base. It lets you abstract your specific problem in a manner that allows it to be compared to other, seemingly unrelated, problems. This allows you to explore solutions that have worked for related abstractions and apply those solutions to your own problem. The methodology is both broad and deep, but this article will take a look at Contradiction Analysis, one of the many tools that are part of the TRIZ toolkit. Contradiction Analysis clarifies the root of, and provides tremendous insight into, the problem you are trying to solve.
Contradiction Analysis
Contradictions were first explored in a dialogue by Plato written in 384 BC. His pupil Aristotle’s law of non-contradiction says that “One cannot say of something that it is and that it is not in the same respect and at the same time”. Clearly, the concept of contradictions is not unique to TRIZ, but the application to engineering problems and the specific formulations of those abstractions is.
In TRIZ there are two forms of contradiction statements. The form that represents the highest level of abstraction, and therefore provides the clearest view of the root problem to be solved, is called a physical (or inherent) contradiction. Capturing a physical (or inherent) contradiction is simple but does required adherence to a particular formulation. That formulation is as follows:
Want a specific situation for the purpose of a specific benefit
-and-
Want the opposite of the original specific situation for the purpose of a different specific benefit.
Some examples are:
- Want a large automobile engine for the purpose of high power AND Want a small engine for the purpose of high gas mileage.
- Want a power cord for the electric lawnmower for the purpose of providing electricity to the machine AND Want no power cord for the electric lawnmower for the purpose of increasing the mobility of the machine.
- Want high temperature water in the clothes washer for the purpose of loosening and dissolving grease AND Want low temperature water in the clothes washer for the purpose of not damaging the clothing.
It turns out that to innovate, one must transcend a limiting situation. Stating the contradictions that characterize the design of a system, or its sub-components, helps us visualize the system’s limiting factors as well as the ways to get around them.
Contradiction Analysis in Action
As far as the automobile engine size is concerned, auto manufacturers only recently started resolving the contradictory requirements of high power versus high gas mileage. Before that, they simply created different designs for different applications, e.g., large engines for sports cars and trucks (high power and low gas mileage) and small engines for sub-compacts (low power and high gas mileage).
The physical (inherent) contradiction statement around the size of the automobile engine clearly shows that we want both a large and small engine at the same time and what the benefits of those opposites are. Within the past few decades, the auto industry has indeed introduced design changes that begin to resolve the contradictory requirements around the size of the engines utilized. For example, in 1979 GM introduced the V8-6-4 engine which deactivated and reactivated cylinders based on instantaneous power needs, thus increasing the overall gas mileage. Hybrid engine vehicles accomplish the same by using a small gas powered engine (higher gas mileage) combined with an electric motor (higher power). And, as of late, auto manufactures are more often turbo-charging small gasoline engines providing higher power when needed but allowing high gas mileage for the reminder of the drive time.
In relation to the electric lawnmower power cord versus no power cord contradiction, the advancement of lithium-ion batteries has allowed battery powered electric lawnmowers to have sufficient power and run time to allow the loss of the traditional extension cord. In the not too distant future, the equipment that is now powered by batteries may be instead powered by wirelessly beamed electricity.
While I have not yet seen clothes washing machines that address the contradictory requirements around the water temperature used during the washing cycle, stating the contradictory requirements (i.e., hot water to loosen and dissolve grease and cold water so as not to damage the clothing), we greatly increase our chances of resolving that contradiction.
When resolving a physical contradiction, we strive to address the contradictory requirements in either space, time, or condition (a.k.a., relationship). For instance, can we separate the contradictory requirements of water temperature in space? Where do we want hot water? In the washing machine. Where do we want cold water? Also, in the washing machine. Since the location requirements for the hot and cold water are the same, it will not be easy to try to separate the contradictory requirements in space.
When do we want hot water? When washing the clothes. When do we want cold water? Also, when washing the clothes. As with separation in space, we have the same requirements for the hot and cold water at the same time. Once again, since the temporal requirements for the hot and cold water are the same, it will not be easy to try to separate the contradictory requirements in time.
This leaves us with separation in condition (or relation). Under what condition (or relationship) do we want hot water? In relation to the grease. Under what condition (or relationship) do we want cold water? In relation to the clothing. Now we have two different answers when testing for the separation of hot and cold water in condition (or relationship). How might we have hot water at the site of the grease but have cold water everywhere else (on the clothing)? The purpose of the hot water is simply to raise the energy level at the site of the grease. Might we be able to accomplish the same by adding a micro-wave generator to the washing machine that is tuned so that the micro-waves are only absorbed by the grease (and not the water or the clothing)? This particular solution may or may not work, but it is intriguing. The main take away from this example, though, is that a potential solution has been generated by capturing the contradictory requirements for both hot and cold water in clothes washing machines. By generating and pursuing several such solutions, we may discover the one that results in a breakthrough innovation.
A Wireless Network Case Study
Now that we understand the basics of contradiction analysis, let’s apply it to a case study in the wireless industry. Suppose that a wireless phone company needs a significant amount of equipment to improve the system’s coverage area, but the company also wants very little equipment because it is expensive.
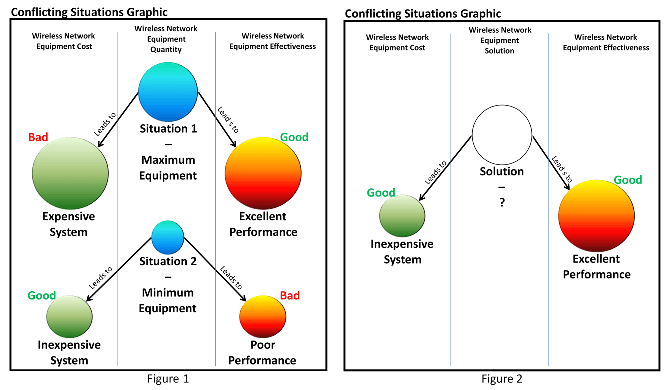
Generally speaking, there are two boundary conditions (existing at the opposite ends of a continuum) that define the range of available solutions to this problem within the restrictions set forth by the existing system design. In other words, based on how our fictitious wireless service provider’s technical systems are designed, there are two extremes defined by the current system limitations and therefore the solution can only exist somewhere between them. Figure 1 shows these two extremes.
- In situation one of Figure 1, the amount of wireless network equipment is at a maximum (large blue circle). This large amount of equipment drives two results: First, the cost of the system (large green circle on the left), which is very high, represents an undesirable situation. Second, the performance (or effectiveness) of the system (large orange circle on the right), which is excellent, represents a desirable situation.
- In situation two of Figure 1, the amount of wireless network equipment is at a minimum (small blue circle). This small amount of equipment drives two results: First, the cost of the system (small green circle on the left), which is very low, represents a desirable situation. Second, the performance (or effectiveness) of the system (small orange circle on the right), which is poor, represents an undesirable situation.
Therefore, the large amount of equipment needed for quality services is in conflict with the small amount of equipment needed for controlling costs. On the one hand the company wants a large amount of cell towers, repeaters, and switching circuits and on the other hand the company does not want to have to pay for any equipment at all. This represents a contradictory requirement that serves as a system limitation. So, the question is: how can the company spend very little on network equipment but have the system perform as if there is a lot of equipment in operation? In order to solve this problem with an innovative solution, it is necessary to resolve the limiting system contradiction.
The abstract model of such a solution is shown in Figure 2. In this diagram, the solution (which is not necessarily just based around equipment quantity) is the “unknown” solution state depicted as a white circle. The yet unknown solution must result in the best of both worlds as reflected in the two previously defined contradiction models (Figure 1). First, the solution should be relatively inexpensive (small green circle at the left in Figure 2), representing a good situation. Second, the solution should have a high level of performance (large orange circle at the right in Figure 2), representing a good situation. Any solution that simultaneously meets the inexpensive and high-performance requirements of the abstract solution model (Figure 2) will be an innovative solution. To resolve the contradictory requirements around the parameter of equipment quantity, we will need to resolve the contradictions.
How can the system simultaneously contain substantial equipment, so it can support the need for wireless services, and very little equipment, to help control costs?
- Where should there be substantial amount of network equipment to increase the coverage area? Where the cell phones need service.
- Where should there be a minimum amount of network equipment to reduce costs? Where there are no, or few, cell phones.
Since there are different answers to the separation in space questions, we may very well be able to separate the contradictory requirements in space. One idea is to design smart phones with repeater capabilities so that the collection of phones in the network are orchestrated to also act as the network itself. The higher the density of the phones, the better the bandwidth and coverage. While this may be a somewhat simplistic case study (driven by the article’s space limitations), it does bring to light a very real problem faced by the wireless service providers. Further, the considered solution space, though seemingly impossible when viewed through the lens of current mobile phone technology, does provide a solution vector that could possibly drive new technologies. Remember, it is also doubtful that the designers of early vacuum tube based computers would have ever imagined that in a mere 60 years most everyone on the planet would be carrying in their pocket a computational device with millions of times more capability.
The Wider Systematic Innovation Toolkit
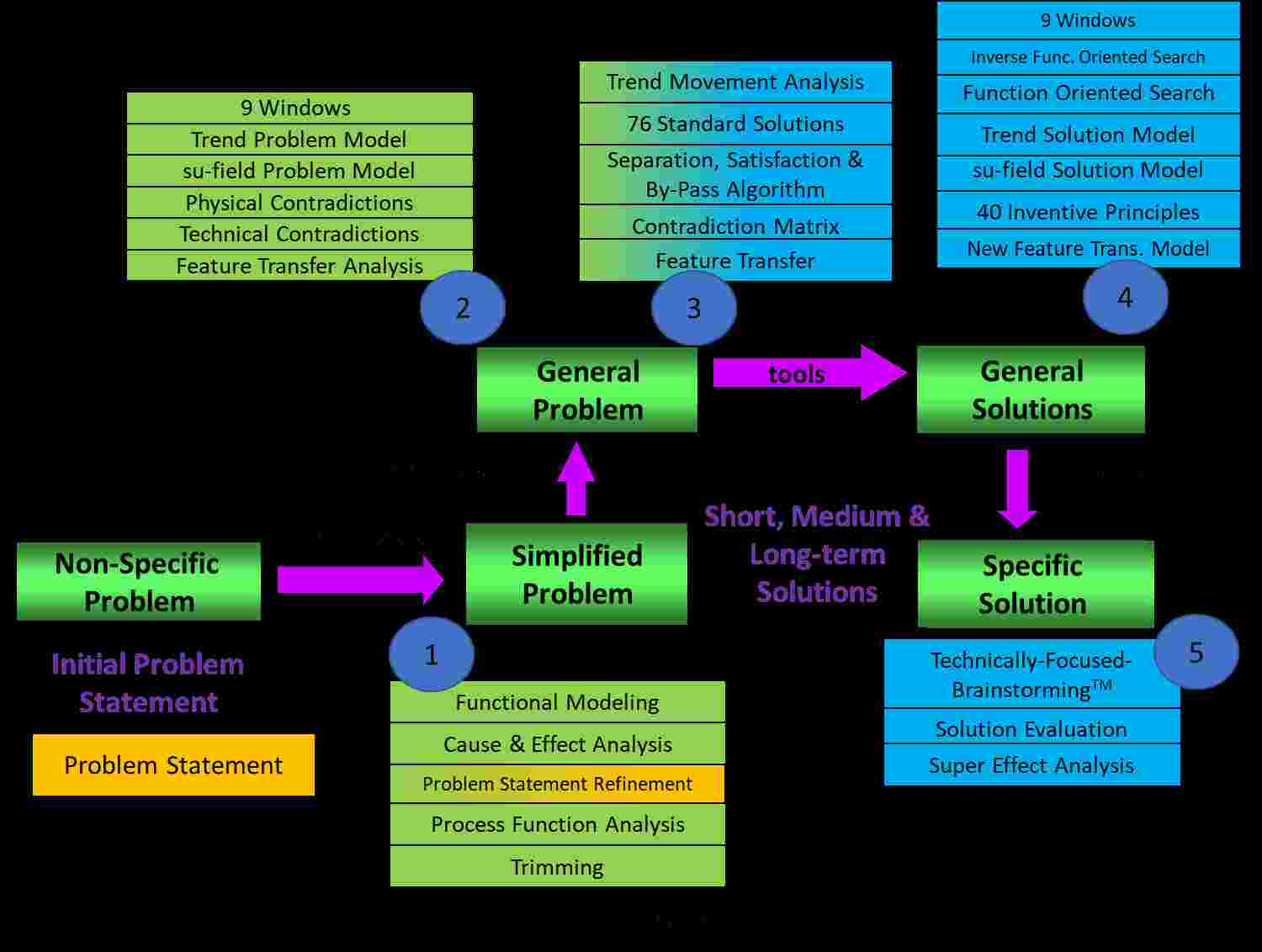
As shown in Figure 3, contradiction analysis is just one of the many techniques leveraged by TRIZ. Moreover, and also shown in Figure 3, the larger category of systematic innovation (SI) contains even more tools. A few of them are listed below. Though only a single problem modeling tool has been presented (i.e., contradiction modeling) in this article, TRIZ offers a host of solution generation tools (see Fig. 3).
Additional SI techniques Included in Step 1 of Figure 3:
- Functional Modeling: A graphical model of a function being performed. Function analysis deals with the entity components that are material objects and are related by way of an action (function) of one of the components on the other. Details what is happening within a complex engineering system.
- Cause and Effect Chains: A graphical model of the analyzed engineering system that reflects the inter-dependence of its disadvantages. Related directly to the associated functional model and details why things are happening within the engineering system.
- Process Function Analysis: A series of linked functional models that details an engineering process and allows the value ranking of all process functions (like Lean on steroids).
Additional TRIZ techniques included in Step 2-4 of Figure 3:
- (Step 2) Technical or Engineering Contradictions: An abstraction of a simplified problem and represents a situation in which an attempt to improve one parameter of an engineering system leads to the worsening of another parameter.
- (Step 3) Contradiction Matrix: A TRIZ tool that allows the identification of specific 40 Principles applicable to the technical contradiction under analysis.
- (Step 4) The 40 Inventive Principles: A problem solving tool that provides generalized recommendations for modifying a system to solve a problem formulated as an technical/engineering or physical contradiction (an inventive principle is an abstract model of the solution to the problem).
- (Steps 2 and 4) Su-field Problem and Solution Models: Symbolic model of a problem or solution formulated in terms of interactions between substances and fields (virtual, real, or improved).
- (Step 3) The 76 Standard Solutions: A set of solutions, in the form of substance-field (Su-field) models, to typical problems that are also expressed in the form of Su-field models.
When employed as an orchestrated set, the SI and TRIZ tools and methods can be used to decompose, abstract, and solve extremely complex and convoluted problems. I personally have used SI and TRIZ to help a national lab develop quantum computing R&D platforms, improve US Air Force satellite control systems and super structures, design ways for the US Army to stop speeding vehicles with little to no damage to the vehicles and no harm to their occupants, advance corn embryo breeding for a world-wide agribusiness, enhance diabetes medications for an international drug company, and improve the utilization rate of operating room suites for Presbyterian Hospitals of New Mexico, to name a few. My very first SI/TRIZ project at Intel Corp. saved the company $250M/year in damage losses to its micro-processor test platforms and an analysis of another 32 projects (executed by my Intel TRIZ students) showed a $1.3 billion impact to Intel’s bottom line. Oh, and guess what, SI/TRIZ is also used for business and organizational problem solving on a regular basis.
TRIZ is the only advanced problem solving methodology that utilizes solution generation engines based on a systematic study of the world-wide patent data base. Perhaps this is why SI/TRIZ is the most powerful problem solving and innovation engine on the planet. If your organization could benefit from a step function improvement in your problem solving and innovation capabilities, I highly recommend that you begin down the exciting and powerful TRIZ pathway. Eogogics offers both courses and consulting to help your organization become a power user of TRIZ. Give us a call!
Editor’s Note: David W. Conley, Eogogics Principal TRIZ faculty, is one of the TRIZ industry’s tier-one experts with International TRIZ Association’s (MATRIZ) Level 4 certification, 15 years as a TRIZ and innovation trainer and practitioner, eight years as the chair of Intel Corp’s world-wide innovation program, 35 years of engineering experience, and 27 years in manufacturing process improvement. David has served on the Executive Board and Certification Committee of the US-based Altshuller Institute for TRIZ Studies. He is the author and presenter of dozens of papers on Systematic Innovation and TRIZ.
Blockchain and Other Cutting Edge Tech

Blockchain, the Distributed Ledger Technology behind Bitcoin, has attracted interest across many industries including financial services, legal, real estate, digital rights, identity management, healthcare, asset tracking, supply chain management, and the Internet of Things (IoT). A disruptive technology, it has the potential to transform the way many transactions are conducted. Eogogics now offers a fast-paced, one-day tutorial on Blockchain for managers and professionals.
Blockchain is just the latest of the 60+ courses and research publications introduced by Eogogics this year, covering such subjects as the Internet of Things (IoT), 5G Wireless Technology, LTE Evolution to 5G Wireless, LTE-Advanced (LTE-A), Software Defined Networking (SDN), Network Functions Virtualization (NFV), Modern Telecommunications, SONET/SDH, Big Data, Artificial Intelligence, Machine-to-Machine (M2M) Communications, Smart Workplace, Connected Home, Smart Cities, Wearable Tech, FinTech, and more. We’ve also updated many of our popular course and workshops for 2017, including Satellite Communications (SATCOM), Root Cause Failure Analysis (RCFA), Geometric Dimensioning and Tolerancing (GD&T), Engineering Creativity, Project Management, Influencing, and Internal Consulting.
So as you dive into your plans and budgets for the year 2017, please keep Eogogics in mind for what we can do to help your organization advance its agenda in 2017. To help you to stretch your budgetary dollars, we’re offering – only till December 16 – 15% off all research publications and 25% off all onsite courses taught in 2017. All online courses are off 50% until then as well. This is an unprecedented offer, limited to first 25 customers in each product line, so be sure to call in early! Course and e-course orders must be called in (1-703-345-4375 or 1-888-364-6442) and onsite courses held down with a deposit by Dec 16, 2016. All discounts are off list prices (minimum class size and other terms apply) and available to both new and returning customers. Call us now to order an e-course or product or schedule an onsite course! Happy budgeting and happy holidays!
Engineering Creativity
This is just a sample of this page's content: View the full page
Articles appearing in various Engineering magazines in support of the Eogogics Engineering Creativity Celebration (March-April 2013)
Product Design and Development Magazine: Unleashing Engineering Creativity Product Design and Development Magazine: Kano Model Design News Magazine: The Engineering Creativity Challenge Product Design and Development Magazine: Nine Screens Technique Product Design and Development Magazine: Concept Fans
Eogogics Workshops on Engineering Creativity
If you are charged with designing new products or processes, or improving existing ones, you’d be interested in our workshops on Unleashing Engineering Creativity. They can help your organization achieve breakthrough results instead of the incremental improvements that are the norm. These workshops, ranging in duration from two to three days, are customized to each client’s engineering environment and are available worldwide.
e-Learning – Unleashing Engineering Creativity
In this exciting 35-minute video, Joe shows you how to overcome self-imposed creativity obstacles and apply TRIZ, the Theory of Inventive Problem Solving, to address real-life engineering challenges. You will also get a feel for our onsite workshops on Unleashing Engineering Creativity. It’s a real course, not ‘sales pitch’, and it’s aimed at engineers, business strategists, business development specialists, and others charged with creating innovative products, processes, or offerings (or improving the existing ones).
Related Courses :
Unleashing Engineering Creativity
Creativity. We deem it essential for business and technical success, yet we are often puzzled about how to find it, how to empower our people to exercise it, and how to apply it. Do we need creativity for solving engineering or business problems, designing completely new products, improving existing products, or developing and improving processes? Are we born with creativity, or do we need to develop our creativity skills?
Related Courses :
Take the Torrance Test of Creativity
Here’s a quick way to assess your creativity based on one of the Torrance tests of creative thinking. Don’t read anything below the tin can yet. Just focus on the tin can below and in one minute list as many uses for it as you can. When you are done making your list, read on.
Related Courses :
Obstacles to Creativity …. And How to Overcome Them!
Creativity obstacles can emerge as the result of structured thinking patterns, timidity, a fear of failure, resource myopia, fear of the unknown, overconfidence, personal and physiological factors, and not knowing how to be creative. This article outlines and recommends approaches for overcoming creativity obstacles.
Related Courses :
Excerpt from the Book
Chapter 1 of Unleashing Engineering Creativity, textbook for the Eogogics Unleashing Engineering Creativity workshop, which is available for presentation worldwide. (You can buy the book separately as well.) The workshop builds on the book with advanced creativity techniques, real world examples, interesting case studies, and stimulating exercises to ensure that the participants thoroughly understand the techniques taught in the course and can apply them on the job.
Podcasts: Unleashing Engineering Creativity
Podcast #1: Introduction Podcast #2: Kano Model
March Madness, Scientific American, and Engineering Creativity

Take a FREE Web class on Unleashing Engineering Creativity (real class, not a sales webinar). It’s FREE, so sign up now!
While the NCAA is celebrating March Madness this month, Scientific American and Eogogics are celebrating Creativity, SciAm with its cover story exploring the evolutionary origins of human creativity and Eogogics with its Engineering Creativity Celebration, starting today and lasting well into April.
An article on the Eogogics website (www.eogogics.com) delves into why we all – engineers and non-engineers alike – are born creative but lose much of that natural creativity by the time we graduate. You don’t have to take my word for it; there is a quick do-it-yourself test of creativity that you can take to validate the truth of this for yourself. Implications of this are enormous: Sans creativity, much of the engineering endeavor amounts to only incremental improvements, not major breakthroughs. Think about what that means in terms of opportunities missed and revenue lost when it comes to designing new products, systems, and processes … or improving existing ones!
So what keeps us from being creative? Another Eogogics article explores the obstacles to creativity and how we can overcome them. The loss of creativity with age notwithstanding, there are well researched and validated techniques we can use to tease more creativity out of us, resulting in a more creative response to a scientific or engineering challenge, be it the design of a product or process or the solution of a problem. For all the well-publicized examples of organizations achieving dramatic results from the use of creativity stimulation techniques, there are many more using these techniques quietly (and profiting from it); however, for the vast majority of technical organizations, these techniques remain an undiscovered secret. There are creativity courses, of course, but they are not developed or taught by engineers/scientists or customized to an organization’s own issues, and the technical community is rightly skeptical of them.
We believe the Eogogics Unleashing Engineering Creativity (“UEC”) Package, the subject of a press release to go out shortly, will change all that. It’s developed and taught by engineers with a lifetime of engineering experience and is extensively field-tested. More than a year in the making, it consists of a three-day hands-on workshop (which can be tailored to include your scientific/engineering challenges) and a lavishly illustrated 170-page textbook created just for the workshop (but also sold separately). You can read more about the workshop and the book on our website, but better yet, take a free 1-hour UEC Mini-workshop on the Web at noon, Eastern on April 25. The mini-workshop, led by Joe Berk, an Eogogics Principal Instructor and author of the UEC book, will discuss how TRIZ, just one of the many techniques taught in the UEC workshop, can be used to solve real engineering challenges. (If you’d like to find out more about TRIZ before attending the mini-workshop, read our article on TRIZ.) We expect this mini-workshop to fill up fast, so you would want to sign up for it early. First 50 to sign up will also be entered into a draw for a free copy of the UEC book. To make things a bit more exciting, Eogogics is also holding an engineering design contest with a couple of prizes worth $1,000 each.
All this and more – including podcasts, screencasts, and videos featuring interviews with technology executives on the subject of creativity – are coming right up in the weeks ahead. The easiest way to find out about all this as it comes out is to connect with us on social media (just click on the icons on top of this page). So get connected, and stay tuned!
Soft Skills
This is just a sample of this page's content: View the full page
What’s Your (Myers Briggs) Type?
Jung noted that we’re always either taking in information (perceiving) or organizing that information and drawing conclusions (judging). Perceiving can involve sensing (what is) or intuition (what could be). Similarly, judging can involve objective considerations (thinking) or its impact on people (feeling).
Related Courses :
Eogogics Professional Development Curricula
Do Guard Dogs Play Basketball?
It’s a story that made the national sports headlines a few years back. It’s a fine example of creative risk-taking as well as teamwork, and one that I often use in my team-work classes.
Related Courses :
MBTI Decision-Making Style Test
How does your decision making style differ from that of your colleagues? Take our brief score-yourself MBTI inventory and find out.
Related Courses :
Eogogics Management Development Curricula
Listening: Are You Listening?
How good are you at listening? Take our quick score-yourself test and find out.
Related Courses :
Give Employees Feedback the Same Way You Want It Given to You
How would your employees like you to provide feedback to them? More than likely, the same way that you’d like it to be given to you by your own boss.
Related Courses :
SOX and Other Compliance Training Bugaboos!
Government regulations and business best practices dictate that you not only conduct certain courses but also maintain records to show that they have been taken and understood by all concerned. Not offering such training can jeopardize the health and safety of your workers, earn the ire of your shareholders, and/or get you on the wrong side of the regulatory authorities.
Related Courses :
Do Guard Dogs Play Basketball?

A high school basketball player got his 15 minutes of fame, but not in the manner he had ever expected. His coach taught the whole team an interesting play but said, “We can only use this once in a lifetime, so be sure you choose the right moment.” Well, that moment came in a championship game with seconds left on the clock. His team had the ball and were down by one. They had to make this shot and were being heavily defended. This young man watched his teammates pass the ball back and forth without being able to penetrate. The clock was ticking. He knew it! This was the moment his coach had talked about in practice many months earlier.
He quickly dropped to his hands and knees and began barking wildly! All defenders turned to him for just a second to see what he was doing. There, on all fours, he just barked and barked like a dog. His distraction allowed his teammate to get inside to the basket and make the final shot to win the game.
When asked after the game why he did that, he said that although he would have rather been the one making the final shot, he was willing to do whatever it took to win the game.
It’s a story that made the national sports headlines a few years back. It’s a fine example of creative risk-taking as well as teamwork, and one that I often use in my team-work classes. If you’ve read or heard about or experienced an incident of this type, please share it with others by posting it to the Eogogics blogs.
Contribution of Eogogics Faculty and Inner Circle Members
This is just a sample of this page's content: View the full page
TRIZ: How to Stimulate Engineering Creativity Using TRIZ
TRIZ is an acronym for teoriza rezhinija izobretatalskih zadach, or the theory of inventive problem solving. The TRIZ technique was developed by Genrich Altshuller, a Russian navy officer who worked in the Soviet patent office. After reviewing 40,000 patents, Altshuller reached the following conclusions: Inventions and innovations follow common patterns that cut across industry and technology boundaries.
Related Courses :
Blockchain and Other Cutting Edge Tech
Blockchain, the Distributed Ledger Technology behind Bitcoin, has attracted interest across many industries including financial services, legal, real estate, digital rights, identity management, healthcare, asset tracking, supply chain management, and the Internet of Things (IoT). A disruptive technology, it has the potential to transform the way many transactions are conducted.
Related Courses :
Do You Support Eunuchs?
Members of the press waited along with company executives and industry dignitaries for the long-anticipated unveiling of the WANG Professional Computer. The newest member of the WANG Laboratories’ computer family was a “blazing fast” MS-DOS machine boasting a 16 bit processor and up to 640 kilobytes of memory – “the most memory”, I recall Bill Gates saying – “that would ever be needed”. The date was April 5th, 1983.
MPLS and the Evolving Telecom Landscape
By 2010 both ATM and FR were in fairly steep decline, relegated to the status of legacy technologies. MPLS usage is growing and new applications for it continue to emerge, making it the technology of choice for most large-scale networks. Nowadays the great buzzword is “cloud computing”, with different versions such as Software as a Service (SaaS—Gmail, Google maps, YouTube, Facebook), Platform as a Service (PaaS—Amazon Elastic Compute Cloud, Windows Azure, Salesforce). All of these utilize MPLS-based networks.
Related Courses :
Computing in the Cloud: A Practical Review
Cloud computing appears simple but is very complex. The apparent simplicity has caused many organizations to move to cloud computing somewhat blindly, driven largely by promises of simplification which will result in cost savings, or just sheer cost savings. Cost savings alone is often enough cause for celebration. And, interestingly, the results achieved by those organizations who “just go for it” are, unexpectedly, usually very positive.
Related Courses :
Distributed Computing for IoT: Data Management in a Fog Computing Environment
Mobile cellular operators are making plans for Mobile Edge Computing (MEC), which enables Cloud computing capabilities and an IT service environment at the edge of the cellular network. It is a concept developed by ETSI (European Telecommunications Standards Institute) that aims to bring computational power into Mobile RAN (radio access network) to promote virtualization of software at the radio edge. MEC brings virtualized applications much closer to mobile users ensuring network flexibility, economy and scalability for improved user experience.
Related Courses :
- Onsite Training: Emerging Technologies, SDN, NFV, Cloud, Blockchain and General Networking
- Onsite Training: 5G Wireless, M2M, IoT, SDN, NFV, Cloud
- Onsite Training: Defense, Security, Public Safety
- Onsite Training: IoT, IPv6, VoIP, EoIP, IMS, MPLS, SNMP
- Onsite Training: M2M, WiFi, Bluetooth, Zig Bee, IoT
Check out our courses on 5G Wireless technologies, applications, and marketplace along with related courses on M2M and IoT.
Obstacles to Creativity …. And How to Overcome Them!
Creativity obstacles can emerge as the result of structured thinking patterns, timidity, a fear of failure, resource myopia, fear of the unknown, overconfidence, personal and physiological factors, and not knowing how to be creative. This article outlines and recommends approaches for overcoming creativity obstacles.
Related Courses :
A “Cheap” Second Opinion
The nature of much of the “training” that Eogogics does has been changing over the last twelve months. I hadn’t really noticed it until a training client brought it up. “This training session is really great”, he said. “It provides a “cheap” second opinion on a lot of our development directions.”
Quantum Telecommunications Demystified

Introduction
There is considerable concern that quantum computing will make existing communications security protocols obsolete. In particular, Public Key Infrastructure (PKI) methods are believed to be vulnerable using the Shor algorithm. This article seeks to familiarize the readers with the new quantum-based technologies and explore their impact on telecommunications, such as PKI. There is much misunderstanding of the capabilities and limitations of these technologies, both theoretical and practical.
People are often mystified by Quantum Telecommunications because of the reputation that Quantum Physics has as a hard discipline. However, it’s possible to understand the basic ideas behind quantum computing and quantum communications without the knowledge of quantum theory, just as it is possible to understand and program computers without the knowledge of solid- state physics. In this article, I will try to show how quantum communications work using simple explanations, illustrations, and analogies. Our emphasis here is on acquiring basic, practical understanding of how the quantum-based technologies work from the vantage point of someone who wants to use them to solve real-world problems, e.g., security in the quantum technology age.
What Is Quantum Telecommunications
Quantum Telecommunications technology is an effort to apply certain quantum theory phenomena and the technology built upon it to create secure communications systems that do not rely on PKI infrastructure. Why? Because of the fear that (at least in theory) PKI can be broken in a reasonable time by quantum computers.
These days, computers and communications are tightly linked. Likewise, quantum computing and quantum communication are closely related and share much of the same technology.
Key Ideas Underlying Quantum Telecommunications
Both quantum computing and quantum communications rely on certain quantum phenomena for their operation. However, a few key ideas are all that’s needed to understand quantum telecommunications:
- Wholeness: Unlike conventional computers, where each circuit element can be analyzed separately, with respect to the equations describing its behavior, in quantum computers and communication systems, the entire system—all of the computing elements — must be analyzed together. There are two aspects to wholeness: entanglement and coherence.
- Entanglement: Entanglement is a property of quantum systems whereby separate pieces act together as one entity, rather than as individual interacting pieces, as happens with conventional circuits and systems. Unlike conventional systems involving interaction, entanglement is (a) much tighter, (b) spatially independent, and (c) not durable. A change in one item of an entangled set can instantaneously affect a change in the others, even when separated by great distances. This spooky “action at a distance” does not, however, violate the Theory of Relativity because it cannot be used to transmit information. Ordinary computer memory bits are entirely independent of each other; setting a bit to “1” has no impact on others. But the opposite is true in quantum computing and communications.
- Coherence: Coherence refers to a single particle or group of entangled particles governed by a single waveform (equation) for their time evolution. Because they are governed by a single waveform, they act as one. Coherence time is the time that this single waveform persists. Coherence is easily broken by random phenomena such as noise, and it can be disrupted by direct action such as measurement of the items in the waveform. It is usually extremely short, on the order of microseconds. But its during periods of coherence that most of the action of quantum devices takes place, which is why coherence time is so important. Note that coherence of particles can be broken but they can remain entangled, though calculations and information transmission would be disrupted.
- No-cloning Theorem. Due to entanglement and coherence, it is not possible to copy a quantum bit (“qubit”) or set of entangled qubits. This is completely different than the case of conventional digital systems, where exact copies of any digital bit string can easily be made at any time.
So how can we take advantage of the quantum properties of entanglement and coherence to secure data in transmission? A very rough analogy would be a team of doctors closely interacting to operate on a patient. Each intuitively and instantly reacts to what the others are doing, so that they can achieve their objective, even if one is working remotely. Coherence time would be the time that they can sustain this intensive cooperation before one says “I need a break”.
The Quantum Bit: Qbit
The key element in quantum computing and communication is the qubit, short for “quantum bit”. Quantum computers are based on the behavior of particles in the subatomic realm, specifically, entanglement and coherence. Although all computer hardware is based on quantum physics, in the case of conventional digital computers and communication, the goal is to suppress many aspects of quantum behavior by suitable device design. In the case of quantum computers and communication, the goal is to utilize certain quantum phenomena to our advantage. In particular, quantum phenomena are harnessed to make the qubit, which serves a function parallel in many ways to the bit in ordinary digital systems.
The qubit is a physical device, operating on quantum principles, used to store one bit of information. However, the qubit differs from ordinary computer bits in that it can be in both states (0 and 1) simultaneously under certain conditions. This isn’t some sort of magic, but a way to describe its behavior. You can’t measure a qubit and say that it is 90% “1” and 10% “0”. What these percentages mean is that each state has a certain probability, and this determines what value the qubit will take when actually measured. A quantum detector, by the laws of physics, can only report a “1” or a “0”; it cannot report percentages of each. For example, if the qubit has a 90% probability of being in the 1 state, and a 10% probability of being in the 0 state, then if we make a measurement, we have a 90% chance of measuring 1, and a 10% chance of measuring 0. This is, of course, totally different than the behavior of ordinary computer bits.
If you want a crude analogy, suppose that a baseball is coming toward you, flashing between red and green very fast. When you catch it, you find that it is either red or green, but not both. If another is thrown at you, when you catch it, you may find that it is the opposite color of the first. If the baseballs have a 90% chance of flashing red and a 10% chance of flashing green, then 9 out of 10 that you catch will be red.
Qubits can be any physical system or entity governed by the laws of quantum theory and capable of being in two states, such as a photon, which can be in a spin up or a spin down state, or both simultaneously. When a qubit is in a mix of states, as long as it remains that way, it is coherent. If it changes state, e.g., goes from 90% to 50% probability of a particular spin, it has lost its coherence. A qubit can be linked to other qubits acting in the same way, so that the entire ensemble behaves as one entangled system while computing is taking place, with all the qubits in both states simultaneously and all governed by the same waveform. When the answer is read, the system “collapses” back to individual values (1 or 0) for each qubit, based on the probabilities of 1 and 0 for each qubit at that moment.
With this background we can now look at quantum communication methods. We will look at two approaches: (1) Quantum Key Distribution or QKD, and (2) Quantum Teleportation. Both are still in the experimental/demonstration phase.
Quantum Key Distribution (QKD)
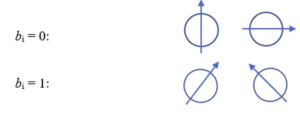
In QKD, data to be transmitted over ordinary networks is encoded as usual with a key and sent. It is only the key itself that involves quantum phenomena. The goal is to allow key sharing or distribution without need for PKI. In the method known as BB84, the encryption key k to be used is a bit string proposed by one person, whom we’ll call Alice. She also generates a random bit string of equal length, we’ll call it b, which determines the basis that will be used to encode each bit of the proposed encryption key. The idea behind the basis is that you have to decide, when sending something like a photon with a spin orientation, what orientation will be considered a “1” and what will be considered a “0”. Typically, two bases are used: the 0° and 90° basis, and the +45° basis. For example, in the 0°/90° basis, we can choose 0° to represent “1” and 90° to represent “0”. In the ±45° basis, we can let +45° represent “1”, and -45° represent “0”. It may seem strange to be randomly changing the basis used for sending bits, but this turns out to be what makes transmission of the key secure. The method also relies on filters on the receiving end which are used to determine the orientation of the qubit sent.
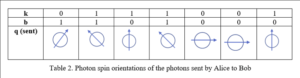
What follows is a high-level sketch of how it works, with minimal mathematics. In practice, many details would need to be worked out. In this simple example we will use very short keys consisting of 7 bits for illustrative purposes. For a real system, Alice and Bob would use 256 to 512 or more.
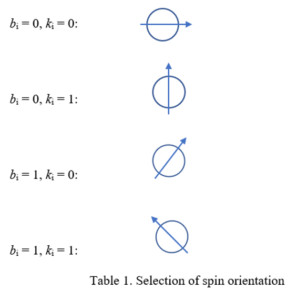
In the first step, as noted, Alice chooses two random bit strings k and b, that each consist of n bits. Her bit string k contains the actual bits she wants to send to Bob (out of which the key will later be formed), while b determines the spin orientation of the quantum particle used to encode each bit. Typically, the orientation is 0 or 90° for one basis, and +45° for the other basis. In quantum terms, these orientations are described as bases. Let the bits of string b be denoted as bi. Then if bi = 0, the first set of orientations will be used. If bi=1, the second set of orientations will be used. So we have:
Now Alice matches the bit ki that she wants to encode with the appropriate spin orientation, according to the scheme in Table 1:
If Alice’s bit string b, the one used for encoding, is b=1101000, and the string k to be encoded is k = 0111001, she would use the sequence of particle spins shown in Table 2, i.e., she would transmit a sequence of particles with these spins to Bob:
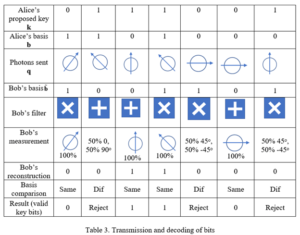
If Bob’s detector for a qubit has the wrong orientation, it will report a “1” 50% of the time, and a “0” 50% of the time. If it has the right orientation, it will report a “1” or “0” as appropriate close to 100% of the time. Due to the fact that Bob’s detectors will only yield a 1 or a 0 even when they have the wrong orientation, Alice will need to transmit q multiple times, let’s say 10 times, for Bob to gauge probabilities.
Bob at the same time prepares his own random bit string, which we shall call b˜= 1001101. This is the set of spin orientations (bases) that Bob will use to filter the photons that he receives from Alice. In practice, what this means is that Bob has a set of filters corresponding to various spin orientations. A “1” in Bob’s bit string means that his filter will pass a ±45° spin orientation, and a “0” in Bob’s bit string means that it will pass a 0 or 90° orientation. Schematically, Bob’s filters would look like this:
If Bob’s detectors consistently give a value of “1” or “0” for a particular qubit sent, Bob can determine exactly which of the two possible orientations it has, and using Table 1, infer which bit value (0 or 1) from Alice’s string k was sent for that bit position. Bob knows which bits had the same basis in his string b˜ and Alice’s string b, because they are the bits for which Bob got a 100% or near 100% likelihood of his answer, 0 or 1. As noted, if he used the wrong filter—assumed the wrong basis — he gets 50% probability for 0 and for 1. Bob then sends Alice, in the clear (preferably by another channel), his list of the index numbers for which he believes that he got correct answers, and Alice can then assume that they have the same basis values (spin orientation and detection filter) for those bits. He does not need to tell her what basis he used for those bits. Then they both can determine which bits are valid and which can be discarded. See Table 3 below. In this case we see that the key would be made up of the non-rejected bits, or 0110. In general, about 50% of the transmitted bits will have to be discarded, so if a key of 256 bits is needed, this will mean that Alice will have to transmit at least 512 bits. Once the key is fixed, Alice and Bob can use it in the normal ways to encode their transmissions. In general, approximately half of the bits transmitted will be useable for the key.
As noted above, for this to work, because of the way the detectors function, Alice must transmit her message to Bob several times, so that Bob has a reasonable chance of determining the 50%/50% cases. Clearly, if the chance of detection are 50% 1 and 50% 0, then the probability that Bob will get all 1s or all 0s after n messages from Alice is the same as flipping a coin n times and getting all heads or all tails, i.e., (½)ˆn. If n = 10, that is about 1/1000; if n = 20, it is about 1 in a million.
As it happens, some bits could be corrupted by noise, or there could be some other problem in the communications system. So as a check, some of the agreed-upon bits of the key are “sacrificed”: Alice sends to Bob the correct values of some of the bits corresponding to the index numbers he earlier sent to her. He can then check that they agree with the values that he determined. The number of bits that must be sacrificed will depend on the expected error rate of the communications system. The sacrificed bits are then removed from the key. Let us say that 10% of the bits of the key are to be checked in this manner. Then an additional 20% more bits must be transmitted by Alice in her original transmission. In practice, Alice might send Bob key message of say 2,000 qubits, of which about 1,000 will be useable for the key. They may choose to sacrifice 10% or 100 to verify successful key transmission.
What Can an Eavesdropper Do?
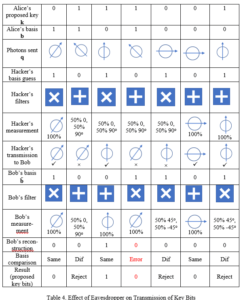
So far, this is not very different than transmitting keys in the usual way. Where does the quantum business come into play? It enters the picture because any would-be eavesdropper is faced with the No-Cloning Theorem, which states that qubits cannot be cloned. That is, you can’t make a copy of one and store it away for future use, as you can with ordinary computer bits. Nor can you copy it, decode one copy, and send the other copy to someone else. If the would-be eavesdropper intercepts a qubit going by, he will collapse its waveform in the process of measuring it. Since he doesn’t know what filter is needed to detect it properly, he’ll have to guess, and he’ll only guess properly 50% of the time, assuming that he knows Table 1. (If he doesn’t, he’ll only guess properly 25% of the time.).
Of course, after the eavesdropper intercepts and decodes a photon, he has to generate and transmit a new photon to Bob so that Bob will not realize that the communications system has been interrupted and compromised. In the cases where the eavesdropper guessed wrong about the filter, he’ll know that it is the opposite of what he guessed, either ±45° or 0/90°, but that is not enough. He will not know which one of those choices is correct for that orientation type. Thus, if he concludes that the correct filter was ±45°, he still doesn’t know if the photon that Alice sent was +45° or -45°. If he could clone the photon, he could then run it through the correct filter and find out which is proper choice. But that is exactly what he cannot do. So the net result is that for approximately half of the bits where his detection yielded 50%, indicating that he chose the wrong filter, he will generate and transmit to Bob a new photon with the wrong spin orientation.
Therefore, the situation is this: For 50% of the photons, he will have correctly guessed the filter orientation, and be able to determine the photon orientation sent by Alice. He can then generate and transmit to Bob a new photon that has the same orientation. For the remaining 50%, his incorrect guessing of the filter orientation will allow him to conclude what the correct orientation type is (“+” or “X”), but not which of the two choices for that orientation is correct. Hence, when he generates a new photon to send to Bob in these cases, 50% of the time it will be incorrect. The net result is that Bob will receive 50%+25%=75% correct photons, and 25% incorrect photons (25% = ½ x ½). See Table 4 for a sample case.
Bob will not be aware yet that he has received incorrect photons, and he will proceed as before to send Alice the indices of what he has concluded are the valid key bits. However, when Alice and Bob “sacrifice” what they believe to be a few good qubits, they will immediately see a high error rate (25%), and realize that their communications channel has been compromised. See Table 5 for the hacker’s reconstruction of the key. On the other hand, if they exchange n sacrificed bits and they are all correct, the chance that this could happen under an eavesdropping scenario is 1/4ˆn. For n = 10, this is 9.5 x 10ˆ(-7), a small number. If they sacrifice 20 bits, the chance is 9.1 x 10ˆ(-13), about one in a trillion, meaning an exceedingly small chance of eavesdropping without it being detected. Thus, they can be confident that their key is secure and correct. If there is a small error rate, say 1-2% of the sacrificed bits are wrong, they can conclude that there was no eavesdropping, but random errors in the communications system. In that case Alice could just repeat her transmission to Bob, more than once if necessary, and combine the results to reduce the errors to whatever value they deem appropriate.
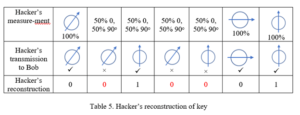
Refer to Table 4 for a concrete example of what may happen with our 7-qubit example.
Because of the hacker, Bob now has some incorrect key bits. He thinks that the key is 0100, with bits 2, 5, and 7 rejected. In this case, if Alice and Bob check bit 4, they would find a discrepancy since Alice intended to transmit a “1”, but Bob believes that bit to be a “0”, even though it is supposed to be acceptable. If they find that their communications have been compromised, they will have to investigate further. It will not do any good to keep transmitting keys, and they have no way of knowing which bits in the key are still secure. Fortunately, however, it is very difficult to tap a fiber optic connection, and usually very easy to pinpoint the location of a tap, if one is made, using an Optical Time Domain Reflectometer (OTDR).
What does the hacker conclude? First of all, remember that just taking random guesses, the hacker could get 50% of the key bits correct, since each can only be a 1 or a 0 and both values have a 50% probability. So how much better can he do with his eavesdropping? Let’s use Table 4 to see what the hacker concludes, assuming that he knows Table 1.
The hacker might conclude that the key is 0010001. In this case the Hacker got 4 out of 7 correct, or 57% of the total. If he tosses the problematic bits, he might conclude 001. In either case he has no way of knowing which of his problematic bits is correct, or even if he has the correct number of bits.
If he is able to intercept Bob’s transmission of bit indices that he thinks are correct, viz. bits 1, 3, 4, 6, the hacker would conclude 0100. The hacker then has 3 out of 4 correct, or 75%, a gain of 25% over random guessing, but far from 100%. That, in general, is what the hacker will be able to do, on account of the 50% error in guessing the orientation of the photons for which he had the wrong filter.
In fact, this is life with quantum computing and communications systems: errors are due to the uncertainties inherent in quantum phenomena, and usually the only practical way to reduce them is to repeat the operation many times and use the Law of Large Numbers to infer convergence. For example, with a key bit, if you get “1” 9 times out of 10 transmissions, you may assume that this is the correct value of that bit. But in some cases, higher degrees of certainty may be needed.
Interestingly, even with PKI, problems can arise. For example, if a hacker is able to penetrate Bob’s computer, he can discover Bob’s secret key, and by intercepting messages sent to Bob, compromise his communications without Bob knowing. To fix this problem, Bob would have to find out how the hacker gained entry into his computer, and make appropriate changes.
QKD networks are commercially available in China, the U.S., South Korea and Europe. They are not extensively used because a facility needs access to a special purpose, optical-fiber network or quantum satellite. Most announcements are of demonstration networks. In February 2022 JPMorgan Chase, Toshiba and Ciena demonstrated what they claim is full viability of a first-of-its-kind Quantum Key Distribution (QKD) network for metropolitan areas. China claims a 2,032 km (1,263 mile) ground line between Shanghai and Bejing. China also claims (2021) to have developed an integrated space-to-ground quantum communication network that combines a large-scale fiber network of more than 700 fiber QKD links and two high-speed satellite-to-ground free-space QKD links.
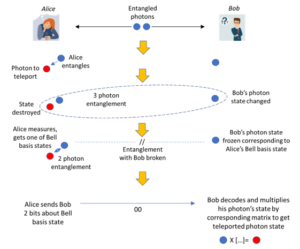
Quantum Teleportation
Quantum Teleportation, unlike QKD, involves sending data entirely in quantum form, using entangled photons. Alice or a third-party generates pairs of entangled photons, one pair for each bit to be sent. Alice keeps one and the other is sent to Bob, who may be thousands of miles away. (This can be done but it is not easy). Alice allows her photon to interact with a special qubit, a “memory qubit”, that holds the bit that she wants to transmit to Bob. This interaction causes a change in the entangled photons’ state, which is measured. Alice’s action collapses the wavefunction of her photon and the qubit, but because her photon is entangled with Bob’s, his photon’s wavefunction collapses instantaneously as well. Though this sounds like instantaneous transmission of information, violating Special Relativity, it is not because Bob does not yet know what bit Alice wants to transmit. For Bob to reconstruct the value of the original qubit, Alice needs to send him the result of her measurement, which will be one of four states, called “Bell basis states”, encoded with two bits in the clear over a fiber optic cable or other classical means, at less than or equal to the speed of light. By comparing this with the state of his photon, he can reconstruct the original qubit value (which was destroyed by Alice’s measurement, so there is no violation of the No-Cloning Theorem). An eavesdropper would not know the state of Bob’s qubit, so the information sent in the clear by Alice would be worthless to him.
Here is a schematic diagram of quantum teleportation:
Now with this method, there is no separate key, as with the QKD method. Instead, quantum phenomena are used to protect each bit of message that Alice sends. Because there are four possible states of the two entangled photons, two bits of information can be transmitted with each qubit.
For quantum teleportation, the ability to keep photons entangled over large distances is essential. This is a difficult problem without repeaters—special quantum repeaters. Unfortunately, such devices are hard to build because of the need to maintain the entanglement. For ordinary telecommunications circuits, repeaters detect the incoming signal and regenerate it, sending out a new signal that is much cleaner than the one received. For quantum systems, this obviously is impossible, since detection would instantly destroy the entanglement.
A complete discussion of quantum repeaters is beyond the scope of this short article, but the basic idea is fairly simple. Instead of detecting the signal at each regeneration point, a single long-distance entanglement is generated using many short-distance entanglements. This is termed “entanglement swapping”. The trick is to store one entangled photon in a quantum memory at each repeater point, and then retransmit it, without using any type of detection. One photon is sent to the memory, the other goes over another line involving Bell State Measurement (BSM), similar to what is done with teleportation. At the present time (2023), no commercial devices are available, but research is continuing and there have been some demonstration projects. In 2020 a demonstration showed 90% accuracy over 44km. This is not yet commercial-grade but does show that the concept will work in practice.
For those whose work requires an understanding of the quantum telecommunications technologies, Eogogics offers a 2-3 day course called Quantum Communications Training. It can be taught onsite at your offices or remotely as a WebLive(TM) (instructor-led online) course. Have a look at the course outline and let us know if this is a course that would interest your team.
Author: Thomas B. Fowler, Sc.D., Eogogics Principal Faculty