Quantum Telecommunications Demystified
Introduction
There is considerable concern that quantum computing will make existing communications security protocols obsolete. In particular, Public Key Infrastructure (PKI) methods are believed to be vulnerable using the Shor algorithm. This article seeks to familiarize the readers with the new quantum-based technologies and explore their impact on telecommunications, such as PKI. There is much misunderstanding of the capabilities and limitations of these technologies, both theoretical and practical.
People are often mystified by Quantum Telecommunications because of the reputation that Quantum Physics has as a hard discipline. However, it’s possible to understand the basic ideas behind quantum computing and quantum communications without the knowledge of quantum theory, just as it is possible to understand and program computers without the knowledge of solid- state physics. In this article, I will try to show how quantum communications work using simple explanations, illustrations, and analogies. Our emphasis here is on acquiring basic, practical understanding of how the quantum-based technologies work from the vantage point of someone who wants to use them to solve real-world problems, e.g., security in the quantum technology age.
What Is Quantum Telecommunications
Quantum Telecommunications technology is an effort to apply certain quantum theory phenomena and the technology built upon it to create secure communications systems that do not rely on PKI infrastructure. Why? Because of the fear that (at least in theory) PKI can be broken in a reasonable time by quantum computers.
These days, computers and communications are tightly linked. Likewise, quantum computing and quantum communication are closely related and share much of the same technology.
Key Ideas Underlying Quantum Telecommunications
Both quantum computing and quantum communications rely on certain quantum phenomena for their operation. However, a few key ideas are all that’s needed to understand quantum telecommunications:
- Wholeness: Unlike conventional computers, where each circuit element can be analyzed separately, with respect to the equations describing its behavior, in quantum computers and communication systems, the entire system—all of the computing elements — must be analyzed together. There are two aspects to wholeness: entanglement and coherence.
- Entanglement: Entanglement is a property of quantum systems whereby separate pieces act together as one entity, rather than as individual interacting pieces, as happens with conventional circuits and systems. Unlike conventional systems involving interaction, entanglement is (a) much tighter, (b) spatially independent, and (c) not durable. A change in one item of an entangled set can instantaneously affect a change in the others, even when separated by great distances. This spooky “action at a distance” does not, however, violate the Theory of Relativity because it cannot be used to transmit information. Ordinary computer memory bits are entirely independent of each other; setting a bit to “1” has no impact on others. But the opposite is true in quantum computing and communications.
- Coherence: Coherence refers to a single particle or group of entangled particles governed by a single waveform (equation) for their time evolution. Because they are governed by a single waveform, they act as one. Coherence time is the time that this single waveform persists. Coherence is easily broken by random phenomena such as noise, and it can be disrupted by direct action such as measurement of the items in the waveform. It is usually extremely short, on the order of microseconds. But its during periods of coherence that most of the action of quantum devices takes place, which is why coherence time is so important. Note that coherence of particles can be broken but they can remain entangled, though calculations and information transmission would be disrupted.
- No-cloning Theorem. Due to entanglement and coherence, it is not possible to copy a quantum bit (“qubit”) or set of entangled qubits. This is completely different than the case of conventional digital systems, where exact copies of any digital bit string can easily be made at any time.
So how can we take advantage of the quantum properties of entanglement and coherence to secure data in transmission? A very rough analogy would be a team of doctors closely interacting to operate on a patient. Each intuitively and instantly reacts to what the others are doing, so that they can achieve their objective, even if one is working remotely. Coherence time would be the time that they can sustain this intensive cooperation before one says “I need a break”.
The Quantum Bit: Qbit
The key element in quantum computing and communication is the qubit, short for “quantum bit”. Quantum computers are based on the behavior of particles in the subatomic realm, specifically, entanglement and coherence. Although all computer hardware is based on quantum physics, in the case of conventional digital computers and communication, the goal is to suppress many aspects of quantum behavior by suitable device design. In the case of quantum computers and communication, the goal is to utilize certain quantum phenomena to our advantage. In particular, quantum phenomena are harnessed to make the qubit, which serves a function parallel in many ways to the bit in ordinary digital systems.
The qubit is a physical device, operating on quantum principles, used to store one bit of information. However, the qubit differs from ordinary computer bits in that it can be in both states (0 and 1) simultaneously under certain conditions. This isn’t some sort of magic, but a way to describe its behavior. You can’t measure a qubit and say that it is 90% “1” and 10% “0”. What these percentages mean is that each state has a certain probability, and this determines what value the qubit will take when actually measured. A quantum detector, by the laws of physics, can only report a “1” or a “0”; it cannot report percentages of each. For example, if the qubit has a 90% probability of being in the 1 state, and a 10% probability of being in the 0 state, then if we make a measurement, we have a 90% chance of measuring 1, and a 10% chance of measuring 0. This is, of course, totally different than the behavior of ordinary computer bits.
If you want a crude analogy, suppose that a baseball is coming toward you, flashing between red and green very fast. When you catch it, you find that it is either red or green, but not both. If another is thrown at you, when you catch it, you may find that it is the opposite color of the first. If the baseballs have a 90% chance of flashing red and a 10% chance of flashing green, then 9 out of 10 that you catch will be red.
Qubits can be any physical system or entity governed by the laws of quantum theory and capable of being in two states, such as a photon, which can be in a spin up or a spin down state, or both simultaneously. When a qubit is in a mix of states, as long as it remains that way, it is coherent. If it changes state, e.g., goes from 90% to 50% probability of a particular spin, it has lost its coherence. A qubit can be linked to other qubits acting in the same way, so that the entire ensemble behaves as one entangled system while computing is taking place, with all the qubits in both states simultaneously and all governed by the same waveform. When the answer is read, the system “collapses” back to individual values (1 or 0) for each qubit, based on the probabilities of 1 and 0 for each qubit at that moment.
With this background we can now look at quantum communication methods. We will look at two approaches: (1) Quantum Key Distribution or QKD, and (2) Quantum Teleportation. Both are still in the experimental/demonstration phase.
Quantum Key Distribution (QKD)
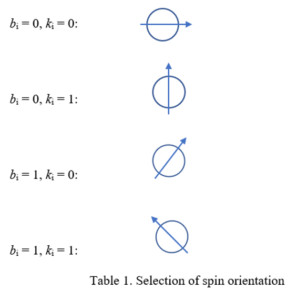
In QKD, data to be transmitted over ordinary networks is encoded as usual with a key and sent. It is only the key itself that involves quantum phenomena. The goal is to allow key sharing or distribution without need for PKI. In the method known as BB84, the encryption key k to be used is a bit string proposed by one person, whom we’ll call Alice. She also generates a random bit string of equal length, we’ll call it b, which determines the basis that will be used to encode each bit of the proposed encryption key. The idea behind the basis is that you have to decide, when sending something like a photon with a spin orientation, what orientation will be considered a “1” and what will be considered a “0”. Typically, two bases are used: the 0° and 90° basis, and the +45° basis. For example, in the 0°/90° basis, we can choose 0° to represent “1” and 90° to represent “0”. In the ±45° basis, we can let +45° represent “1”, and -45° represent “0”. It may seem strange to be randomly changing the basis used for sending bits, but this turns out to be what makes transmission of the key secure. The method also relies on filters on the receiving end which are used to determine the orientation of the qubit sent.
What follows is a high-level sketch of how it works, with minimal mathematics. In practice, many details would need to be worked out. In this simple example we will use very short keys consisting of 7 bits for illustrative purposes. For a real system, Alice and Bob would use 256 to 512 or more.
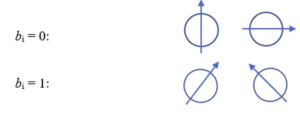
In the first step, as noted, Alice chooses two random bit strings k and b, that each consist of n bits. Her bit string k contains the actual bits she wants to send to Bob (out of which the key will later be formed), while b determines the spin orientation of the quantum particle used to encode each bit. Typically, the orientation is 0 or 90° for one basis, and +45° for the other basis. In quantum terms, these orientations are described as bases. Let the bits of string b be denoted as bi. Then if bi = 0, the first set of orientations will be used. If bi=1, the second set of orientations will be used. So we have:
Now Alice matches the bit ki that she wants to encode with the appropriate spin orientation, according to the scheme in Table 1:
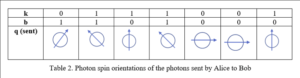
If Alice’s bit string b, the one used for encoding, is b=1101000, and the string k to be encoded is k = 0111001, she would use the sequence of particle spins shown in Table 2, i.e., she would transmit a sequence of particles with these spins to Bob:
If Bob’s detector for a qubit has the wrong orientation, it will report a “1” 50% of the time, and a “0” 50% of the time. If it has the right orientation, it will report a “1” or “0” as appropriate close to 100% of the time. Due to the fact that Bob’s detectors will only yield a 1 or a 0 even when they have the wrong orientation, Alice will need to transmit q multiple times, let’s say 10 times, for Bob to gauge probabilities.
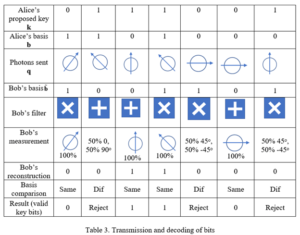
Bob at the same time prepares his own random bit string, which we shall call b˜= 1001101. This is the set of spin orientations (bases) that Bob will use to filter the photons that he receives from Alice. In practice, what this means is that Bob has a set of filters corresponding to various spin orientations. A “1” in Bob’s bit string means that his filter will pass a ±45° spin orientation, and a “0” in Bob’s bit string means that it will pass a 0 or 90° orientation. Schematically, Bob’s filters would look like this:
If Bob’s detectors consistently give a value of “1” or “0” for a particular qubit sent, Bob can determine exactly which of the two possible orientations it has, and using Table 1, infer which bit value (0 or 1) from Alice’s string k was sent for that bit position. Bob knows which bits had the same basis in his string b˜ and Alice’s string b, because they are the bits for which Bob got a 100% or near 100% likelihood of his answer, 0 or 1. As noted, if he used the wrong filter—assumed the wrong basis — he gets 50% probability for 0 and for 1. Bob then sends Alice, in the clear (preferably by another channel), his list of the index numbers for which he believes that he got correct answers, and Alice can then assume that they have the same basis values (spin orientation and detection filter) for those bits. He does not need to tell her what basis he used for those bits. Then they both can determine which bits are valid and which can be discarded. See Table 3 below. In this case we see that the key would be made up of the non-rejected bits, or 0110. In general, about 50% of the transmitted bits will have to be discarded, so if a key of 256 bits is needed, this will mean that Alice will have to transmit at least 512 bits. Once the key is fixed, Alice and Bob can use it in the normal ways to encode their transmissions. In general, approximately half of the bits transmitted will be useable for the key.
As noted above, for this to work, because of the way the detectors function, Alice must transmit her message to Bob several times, so that Bob has a reasonable chance of determining the 50%/50% cases. Clearly, if the chance of detection are 50% 1 and 50% 0, then the probability that Bob will get all 1s or all 0s after n messages from Alice is the same as flipping a coin n times and getting all heads or all tails, i.e., (½)ˆn. If n = 10, that is about 1/1000; if n = 20, it is about 1 in a million.
As it happens, some bits could be corrupted by noise, or there could be some other problem in the communications system. So as a check, some of the agreed-upon bits of the key are “sacrificed”: Alice sends to Bob the correct values of some of the bits corresponding to the index numbers he earlier sent to her. He can then check that they agree with the values that he determined. The number of bits that must be sacrificed will depend on the expected error rate of the communications system. The sacrificed bits are then removed from the key. Let us say that 10% of the bits of the key are to be checked in this manner. Then an additional 20% more bits must be transmitted by Alice in her original transmission. In practice, Alice might send Bob key message of say 2,000 qubits, of which about 1,000 will be useable for the key. They may choose to sacrifice 10% or 100 to verify successful key transmission.
What Can an Eavesdropper Do?
So far, this is not very different than transmitting keys in the usual way. Where does the quantum business come into play? It enters the picture because any would-be eavesdropper is faced with the No-Cloning Theorem, which states that qubits cannot be cloned. That is, you can’t make a copy of one and store it away for future use, as you can with ordinary computer bits. Nor can you copy it, decode one copy, and send the other copy to someone else. If the would-be eavesdropper intercepts a qubit going by, he will collapse its waveform in the process of measuring it. Since he doesn’t know what filter is needed to detect it properly, he’ll have to guess, and he’ll only guess properly 50% of the time, assuming that he knows Table 1. (If he doesn’t, he’ll only guess properly 25% of the time.).
Of course, after the eavesdropper intercepts and decodes a photon, he has to generate and transmit a new photon to Bob so that Bob will not realize that the communications system has been interrupted and compromised. In the cases where the eavesdropper guessed wrong about the filter, he’ll know that it is the opposite of what he guessed, either ±45° or 0/90°, but that is not enough. He will not know which one of those choices is correct for that orientation type. Thus, if he concludes that the correct filter was ±45°, he still doesn’t know if the photon that Alice sent was +45° or -45°. If he could clone the photon, he could then run it through the correct filter and find out which is proper choice. But that is exactly what he cannot do. So the net result is that for approximately half of the bits where his detection yielded 50%, indicating that he chose the wrong filter, he will generate and transmit to Bob a new photon with the wrong spin orientation.
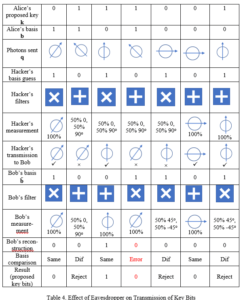
Therefore, the situation is this: For 50% of the photons, he will have correctly guessed the filter orientation, and be able to determine the photon orientation sent by Alice. He can then generate and transmit to Bob a new photon that has the same orientation. For the remaining 50%, his incorrect guessing of the filter orientation will allow him to conclude what the correct orientation type is (“+” or “X”), but not which of the two choices for that orientation is correct. Hence, when he generates a new photon to send to Bob in these cases, 50% of the time it will be incorrect. The net result is that Bob will receive 50%+25%=75% correct photons, and 25% incorrect photons (25% = ½ x ½). See Table 4 for a sample case.
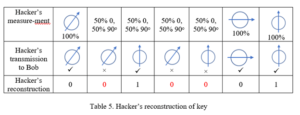
Bob will not be aware yet that he has received incorrect photons, and he will proceed as before to send Alice the indices of what he has concluded are the valid key bits. However, when Alice and Bob “sacrifice” what they believe to be a few good qubits, they will immediately see a high error rate (25%), and realize that their communications channel has been compromised. See Table 5 for the hacker’s reconstruction of the key. On the other hand, if they exchange n sacrificed bits and they are all correct, the chance that this could happen under an eavesdropping scenario is 1/4ˆn. For n = 10, this is 9.5 x 10ˆ(-7), a small number. If they sacrifice 20 bits, the chance is 9.1 x 10ˆ(-13), about one in a trillion, meaning an exceedingly small chance of eavesdropping without it being detected. Thus, they can be confident that their key is secure and correct. If there is a small error rate, say 1-2% of the sacrificed bits are wrong, they can conclude that there was no eavesdropping, but random errors in the communications system. In that case Alice could just repeat her transmission to Bob, more than once if necessary, and combine the results to reduce the errors to whatever value they deem appropriate.
Refer to Table 4 for a concrete example of what may happen with our 7-qubit example.
Because of the hacker, Bob now has some incorrect key bits. He thinks that the key is 0100, with bits 2, 5, and 7 rejected. In this case, if Alice and Bob check bit 4, they would find a discrepancy since Alice intended to transmit a “1”, but Bob believes that bit to be a “0”, even though it is supposed to be acceptable. If they find that their communications have been compromised, they will have to investigate further. It will not do any good to keep transmitting keys, and they have no way of knowing which bits in the key are still secure. Fortunately, however, it is very difficult to tap a fiber optic connection, and usually very easy to pinpoint the location of a tap, if one is made, using an Optical Time Domain Reflectometer (OTDR).
What does the hacker conclude? First of all, remember that just taking random guesses, the hacker could get 50% of the key bits correct, since each can only be a 1 or a 0 and both values have a 50% probability. So how much better can he do with his eavesdropping? Let’s use Table 4 to see what the hacker concludes, assuming that he knows Table 1.
The hacker might conclude that the key is 0010001. In this case the Hacker got 4 out of 7 correct, or 57% of the total. If he tosses the problematic bits, he might conclude 001. In either case he has no way of knowing which of his problematic bits is correct, or even if he has the correct number of bits.
If he is able to intercept Bob’s transmission of bit indices that he thinks are correct, viz. bits 1, 3, 4, 6, the hacker would conclude 0100. The hacker then has 3 out of 4 correct, or 75%, a gain of 25% over random guessing, but far from 100%. That, in general, is what the hacker will be able to do, on account of the 50% error in guessing the orientation of the photons for which he had the wrong filter.
In fact, this is life with quantum computing and communications systems: errors are due to the uncertainties inherent in quantum phenomena, and usually the only practical way to reduce them is to repeat the operation many times and use the Law of Large Numbers to infer convergence. For example, with a key bit, if you get “1” 9 times out of 10 transmissions, you may assume that this is the correct value of that bit. But in some cases, higher degrees of certainty may be needed.
Interestingly, even with PKI, problems can arise. For example, if a hacker is able to penetrate Bob’s computer, he can discover Bob’s secret key, and by intercepting messages sent to Bob, compromise his communications without Bob knowing. To fix this problem, Bob would have to find out how the hacker gained entry into his computer, and make appropriate changes.
QKD networks are commercially available in China, the U.S., South Korea and Europe. They are not extensively used because a facility needs access to a special purpose, optical-fiber network or quantum satellite. Most announcements are of demonstration networks. In February 2022 JPMorgan Chase, Toshiba and Ciena demonstrated what they claim is full viability of a first-of-its-kind Quantum Key Distribution (QKD) network for metropolitan areas. China claims a 2,032 km (1,263 mile) ground line between Shanghai and Bejing. China also claims (2021) to have developed an integrated space-to-ground quantum communication network that combines a large-scale fiber network of more than 700 fiber QKD links and two high-speed satellite-to-ground free-space QKD links.
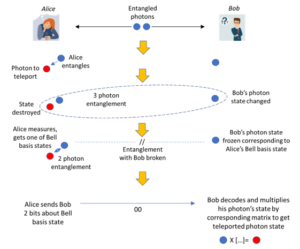
Quantum Teleportation
Quantum Teleportation, unlike QKD, involves sending data entirely in quantum form, using entangled photons. Alice or a third-party generates pairs of entangled photons, one pair for each bit to be sent. Alice keeps one and the other is sent to Bob, who may be thousands of miles away. (This can be done but it is not easy). Alice allows her photon to interact with a special qubit, a “memory qubit”, that holds the bit that she wants to transmit to Bob. This interaction causes a change in the entangled photons’ state, which is measured. Alice’s action collapses the wavefunction of her photon and the qubit, but because her photon is entangled with Bob’s, his photon’s wavefunction collapses instantaneously as well. Though this sounds like instantaneous transmission of information, violating Special Relativity, it is not because Bob does not yet know what bit Alice wants to transmit. For Bob to reconstruct the value of the original qubit, Alice needs to send him the result of her measurement, which will be one of four states, called “Bell basis states”, encoded with two bits in the clear over a fiber optic cable or other classical means, at less than or equal to the speed of light. By comparing this with the state of his photon, he can reconstruct the original qubit value (which was destroyed by Alice’s measurement, so there is no violation of the No-Cloning Theorem). An eavesdropper would not know the state of Bob’s qubit, so the information sent in the clear by Alice would be worthless to him.
Here is a schematic diagram of quantum teleportation:
Now with this method, there is no separate key, as with the QKD method. Instead, quantum phenomena are used to protect each bit of message that Alice sends. Because there are four possible states of the two entangled photons, two bits of information can be transmitted with each qubit.
For quantum teleportation, the ability to keep photons entangled over large distances is essential. This is a difficult problem without repeaters—special quantum repeaters. Unfortunately, such devices are hard to build because of the need to maintain the entanglement. For ordinary telecommunications circuits, repeaters detect the incoming signal and regenerate it, sending out a new signal that is much cleaner than the one received. For quantum systems, this obviously is impossible, since detection would instantly destroy the entanglement.
A complete discussion of quantum repeaters is beyond the scope of this short article, but the basic idea is fairly simple. Instead of detecting the signal at each regeneration point, a single long-distance entanglement is generated using many short-distance entanglements. This is termed “entanglement swapping”. The trick is to store one entangled photon in a quantum memory at each repeater point, and then retransmit it, without using any type of detection. One photon is sent to the memory, the other goes over another line involving Bell State Measurement (BSM), similar to what is done with teleportation. At the present time (2023), no commercial devices are available, but research is continuing and there have been some demonstration projects. In 2020 a demonstration showed 90% accuracy over 44km. This is not yet commercial-grade but does show that the concept will work in practice.
For those whose work requires an understanding of the quantum telecommunications technologies, Eogogics offers a 2-3 day course called Quantum Communications Training. It can be taught onsite at your offices or remotely as a WebLive(TM) (instructor-led online) course. Have a look at the course outline and let us know if this is a course that would interest your team.
Author: Thomas B. Fowler, Sc.D., Eogogics Principal Faculty



Sorry, comments for this entry are closed at this time.